An odd remedy for one of the most peculiar bugs we have come across recently.
An unruly bug that was causing havoc on Windows systems has been fixed by Microsoft. The bug was occurring on Windows 10 and 11 machines, and it was installing the HP Smart Ppp on Windows machines without permission. It was also renaming any printers it could find to make them HP machines, even though HP did not make them.
What is really strange about this situation, though, is that Microsoft resolved the issue rather than patching Windows Update or creating a hotfix. Instead, the company released the Microsoft Printer Metadata Troubleshooter Tool, an independent tool that scans your system, fixes any renamed printers (which, presumably, would be renamed HP LaserJet M101-M106), fixes any rebadged icons, and gets rid of the HP Smart App (ironic name, that). All of this is expected behavior, but you can not just download and run this program; instead, you have to use administrator credentials to run it.
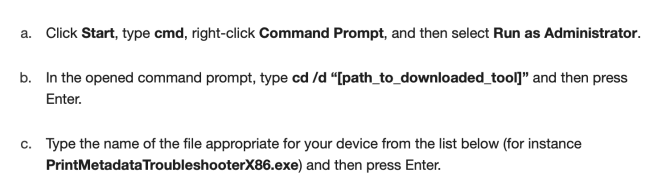
If the tool is successfully run, it will return a “Troubleshooter completed successfully” message if incorrect printer information is found and fixed. If your computer is not affected, it will return the message “Troubleshooter not applicable since metadata package not found.” According to Microsoft, enterprise users must run the tool as the Local System Account. The instructions shown above are for people who are managing their own printers.
Although Windows Central reports that the bug only caused annoyance for users who found software on their system that they had forgotten to install, we would immediately suspect that this was malware. Nevertheless, even though Microsoft claims that affected printers should still function, some users have reported that their printer’s advanced features have been locked out due to renaming.
It implies that although this bug seems silly on the surface, it broke something deep within Windows, even though it is relatively benign. This is implied by the fact that it requires another tool to be downloaded and executed via Command Prompt, which is something the average user would not know how to do.

