Security company Kaspersky claims that using an attack it has named “Triangulation,” unidentified parties were able to completely compromise many iPhones that belonged to its staff.
In spite of the best efforts of companies such as Apple, Google, Microsoft, and others, the majority of the gadgets that we use on a daily basis have significant security flaws. Every day of our life, we live in the hope that the good guys will discover these weaknesses before the bad guys on the internet do. This was not the case in the case of a malware campaign that was specifically targeted across Russia. Kaspersky, a company that specialises in security, has reported that a number of iPhones belonging to its staff were broken into by unknown individuals using a method that it has referred to as “Triangulation.” It is interesting to note that this hacking attempt was only successfully carried out because of the strange and undocumented characteristics of Apple’s ARM-based processors.
Triangulation was only brought to Kaspersky’s attention a few months ago, in spite of the fact that the company believes the attacks had been going on for around four years. During that time period, the attackers were successful in compromising at least a few dozen mobile devices, but it could have been a far larger number. Attackers are able to gain complete access to the system when they use this strategy. Everything is on the table, including stealing data and running programmes remotely. The company has released information on processes, files, and system behaviours that can indicate a Triangulation infection; nonetheless, even experienced security experts have had difficulty recognising the indicators of this sophisticated malware.
A deviously intricate infection chain that contains four zero-day exploits is the foundation upon which triangulation is built. A malicious PDF file is the starting point for the infection. This PDF file makes use of a vulnerability (CVE-2023-41990) in the TrueType font in order to execute limited code. Additionally, it makes use of a memory corruption bug (CVE-2023-32434) and a vulnerability in Safari that enables the virus to execute shell code (CVE-2023-32435). But if it weren’t for the vulnerability known as CVE-2023-38606, none of this would have been able to put a dent in Apple’s security capabilities.
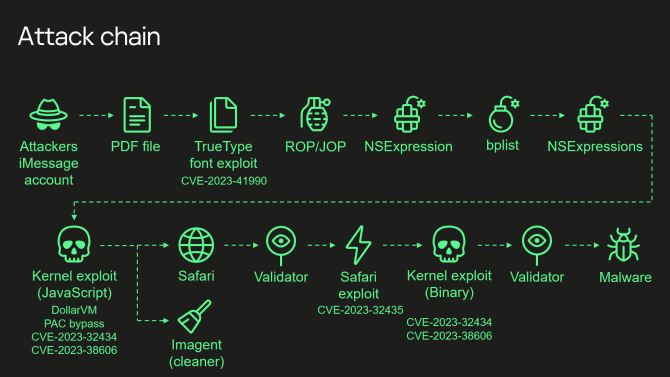
Apple’s secret sauce is exploited by the previously mentioned vulnerability. Due to the fact that the malware presented itself despite Apple’s hardware-based memory protections, it took Kaspersky several months of reverse engineering to figure out what was going on with Triangulation. This function is designed to prevent malicious software from accessing active memory and kernel code, which has the potential to reverse an infection before it even begins. However, Triangulation is able to circumvent this and take complete control of the phone by gaining access to Memory-mapped Input/Outputs (MMIO) that have not been well described. It is possible, according to Kaspersky, that Apple utilised this technology for the purpose of debugging during the engineering process or at the factory. However, it also provided Triangulation with a means to circumvent Apple’s security measures. It is impossible for the researchers to rule out the possibility that this functionality was accidentally left activated.
In light of the fact that Apple was unaware of these vulnerabilities, the attackers were able to take advantage of them in order to acquire low-level access to devices. Additionally, Kaspersky claims that it discovered versions of Triangulation that were intended for the iPad, Apple TV, Apple Watch, and Macs. This is not limited to the iPhone as well. An attack of this level of sophistication leads one to believe that state actors are responsible for it. These actors would have the resources necessary to locate and exploit valuable system weaknesses such as triangulation.
Triangulation was able to be used by the attackers for a considerable amount of time before Kaspersky became conscious of its existence. In response to the discovery made by Kaspersky, the Russian National Coordination Centre for Computer Incidents pointed the blame at the National Security Agency of the United States of America; however, it did not give any proof to support the accusation. Having said that, there is a precedent for not doing so. According to the organisation, triangulation was discovered on thousands of iPhones that belonged to professionals working in diplomatic and embassy settings.
Those individuals who were responsible for Triangulation will now be required to locate a new toy. In recent software releases, Apple has implemented patches to address the vulnerabilities. But now that the exploits are known, it’s possible that other people will try to utilise them. As long as you keep your gadgets up to date, you shouldn’t have to worry about triangulation.

