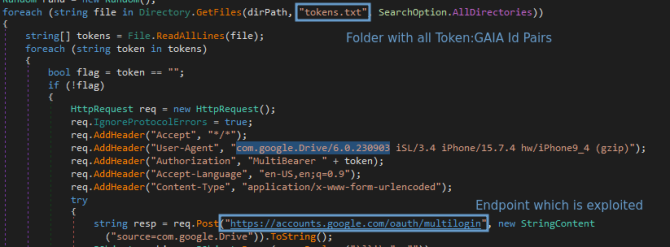
The exploit takes use of an undocumented Google feature called “MultiLogin” that keeps your account updated.
There are numerous aspects of your digital life that are influenced by the search giant Google, especially if you use the services that it offers. All of your data is synchronized across all of Google’s services so that you can stay connected. They have developed a means to remain logged into a stolen Google account even if the password is reset, according to security researchers who report that this functionality has been co-opted by threat actors.
The Google Sync service is dependent on an OAuth endpoint that is not disclosed and is referred to as MultiLogin. An individual who goes by the name PRISMA, a hacker, presented this method on Telegram in October of the previous year. Since that time, it has been found in a number of different data stealer malware-as-a-service clients, such as Lumma, RisePro, and WhiteSnake, among others.
The Chrome browser will save a token that will allow it to remain logged in whenever you log in to Chrome. Malware frequently seeks to steal login tokens since doing so enables the attacker to gain access to your account even if they do not know the password. Apparently, Google’s MultiLogin makes the login cookies a far more appealing target than they would have been otherwise. For the purpose of gaining a deeper comprehension of the ways in which threat actors are using MultiLogin, the security company CloudSEK was successful in reverse engineering a new variant of the Lumma stealer virus.
Tokens for authentication can be regenerated by the MultiLogin endpoint whenever they are required. Changing your Google password, for instance, may be accomplished in this manner without requiring you to log out of all remaining sessions. Simply said, the token is regenerated on your workstation using a pair of tokens known as the GAIA ID and encrypted_token. However, the PRISMA approach enables the tokens to be regenerated an endless number of times, despite the fact that you are only meant to be allowed to do this once.
Although Google is aware of the threat, the company is unable to simply disable the MultiLogin endpoint itself. According to the statement, any affected accounts that were discovered have been restored, and the company is continuously updating its security in order to make these attacks more difficult. It should be brought to your attention that this vulnerability is not a stand-alone one. Despite this, an adversary must first exploit a vulnerability in order to obtain access to the computer system and then steal the required information. If a criminal operating online has access to your device to that extent, then a compromised Google account is simply one of several things that you should be concerned about. By stealing cryptocurrency wallets, the majority of these malware-as-a-service apps are able to generate a profit more quickly.
Despite the fact that threat actors who use this method can continue to access your account even after you change your password, there is a simple solution to prevent them from accomplishing this. A list of all sessions that are currently logged in can be found inside the settings of a Google account. You are able to manually disconnect anything from that location, including a hacker who has your tokens in their possession. If you want to be extra cautious, you can also use the devices panel to sign out of all of your devices.